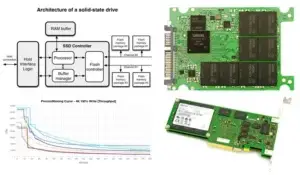
Volatile Memory Leakage in SSDs: How Scratch Pads Can Leak Secrets
The digital age no longer limits security breaches to software vulnerabilities and phishing scams. Volatile memory leakage occurs through physical memory, which computers use daily,


The digital age no longer limits security breaches to software vulnerabilities and phishing scams. Volatile memory leakage occurs through physical memory, which computers use daily,
As the Technical Consultant and Lead Developer on the national eLearning initiative for the health sector, I played a central role in designing, coordinating, and
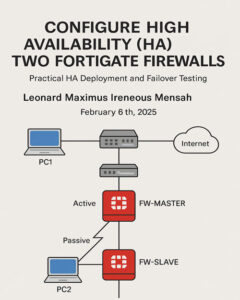
In this project, I configured High Availability (HA) between two FortiGate firewalls to ensure continuous network service during device failure. I began by placing and
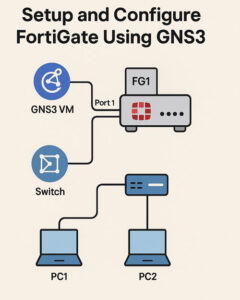
In this project, I deployed and configured a FortiGate firewall using GNS3 to simulate a realistic network environment. I began by changing the firewall hostname

In this project, I conducted a malware analysis investigation focused on unusual network traffic within an organization. Using the provided PCAP file, I identified the

In this project, I configured and managed various Exchange Server messaging components for a corporate environment. I started by logging into the Exchange Admin Center

In this project, I served as the Technical Consultant overseeing the evaluation, selection, and deployment of Learning Management Systems (LMS) for Health Training Institutions (HTIs)

In this project, I installed and configured Snort on a Kali Linux virtual machine to operate as an Intrusion Detection System (IDS). I began by

In this project, I conducted a vulnerability scan on a web server using Nikto to identify critical security risks. I started by launching the Metasploitable2