Volatile Memory Leakage in SSDs: How Scratch Pads Can Leak Secrets

Volatile Memory Leakage in SSDs: How Scratch Pads Can Leak Secrets
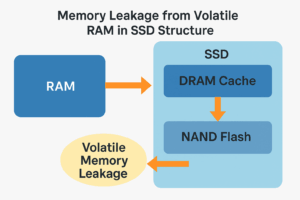 The digital age no longer limits security breaches to software vulnerabilities and phishing scams. Volatile memory leakage occurs through physical memory, which computers use daily, especially when RAM and SSDS experience data loss. This article investigates the occurrence of this security breach, together with attacker methods and prevention strategies.
The digital age no longer limits security breaches to software vulnerabilities and phishing scams. Volatile memory leakage occurs through physical memory, which computers use daily, especially when RAM and SSDS experience data loss. This article investigates the occurrence of this security breach, together with attacker methods and prevention strategies.
How Your Computer Works:
In the following analogy, your computer functions like a kitchen.
- System RAM = Countertop
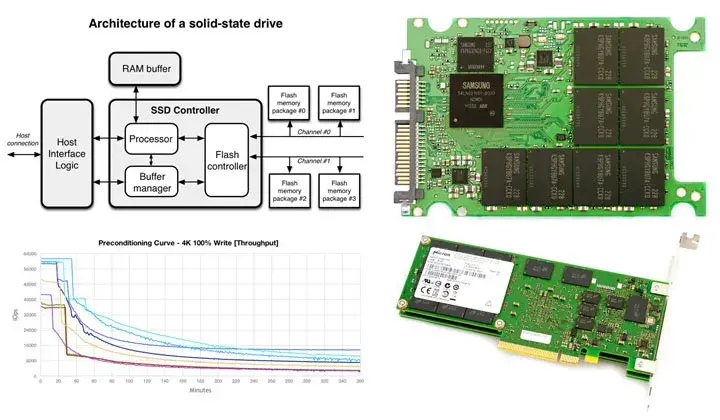
Your system temporarily places data in this space during operation, similar to how you prepare ingredients. - SSD DRAM Cache = Prep Area
The system uses this high-speed temporary storage area to maintain ingredients (data) before it moves them to long-term storage. - SSD NAND Flash = Fridge
The permanent storage of completed data exists in the NAND Flash section, which functions like a refrigerator.
You should clean your countertop and prep area properly to prevent data remnants from being accessed by anyone who enters. The fundamental aspect of volatile memory leakage consists of the forgotten cleanup of these areas.
What Is Volatile Memory?
The memory which loses its content when a system receives a power shutdown belongs to the volatile memory category. This includes:
- RAM (Random Access Memory)
- SSD DRAM Cache (used in many modern SSDS for fast read/write operations)
Note that the above memory areas often contain many sensitive items, which include:
- Passwords
- Encryption keys
- Session tokens
- Fragments of documents
Data stored in volatile memory should be cleared after shutdown. However, they may persist for short periods or longer under specific conditions, thus providing attackers with a brief opportunity to extract it.
⚙️ How Leakage Happens: Step-by-Step
- The operating system retrieves files during the opening process. The system routes file data through the DRAM cache of the SSD when performing save or modification operations.
- Saving or modifying the file: The data passes through the SSD’s DRAM cache for faster processing.
- Attacker intervenes: The system’s data will be exposed if an attacker gains control before the system shuts down.
💡 Technical Note: System-level memory commands like:
sync && echo 3 > /proc/sys/vm/drop_caches
This only affects OS memory, not the SSD’s internal DRAM cache.
How Threat Actors Exploit It
- Cold Boot Attacks: An attacker shuts down the machine before using a USB live operating system to perform a quick reboot. Memory contents (especially RAM) can remain readable for up to 60 seconds, and even longer if cooled. The memory analysis tools Volatility, Lime and WinPmem enable the extraction and analysis of the data.
- DMA Attacks (Direct Memory Access): When devices use Thunderbolt, PCIe or FireWire connections, they bypass operating system permissions to read memory contents directly. The system enables direct access to DRAM cache memory so attackers can conduct reading operations.
- Malware-Based Dumping: Advanced malware programs with administrative rights can conduct real-time memory dumps by searching for specific phrases, like “BEGIN RSA PRIVATE KEY” and embedded session information.
- Firmware Exploitation: Firmware which attackers modify through reverse-engineering enables silent leaking and mirroring of DRAM cache contents.
Technical Insight:
Windows: The malware depends on the NtReadVirtualMemory() function to access memory areas.
The /dev/mem and /proc/<pid>/mem interfaces enable Linux attackers to access physical memory.
Example Scenario: A Real-World Attack
Jody uses TrueCrypt encryption when she mounts her encrypted volume. During work time, the encryption key resides in RAM and spends short periods in the SSD DRAM cache while performing file operations. Jaison, the attacker, creates a system crash and performs a system reboot using a Kali Linux USB device. She runs:
volatility -f memory.dmp –profile=Win7SP1x64 hashdump
This volatility command uses memory.dmp as input to analyse the Windows 7 SP1 x64 profile for hashdump extraction. The extracted password hashes enable offline cracking, which results in unauthorised access to Jody’s encrypted files.
How to Protect Against This Threat
- Use Full-Disk Encryption (FDE) : Windows: BitLocker requires a combination of TPM and PIN for activation.
manage-bde -protectors -add C: -TPMAndPIN
- Enable Memory Scrubbing at Shutdown
Windows: Enable via Group Policy
System > Shutdown: Clear virtual memory pagefile - Select DRAM-less SSDS as the storage option. -Modern DRAM-less drives use Host Memory Buffer (HMB) to eliminate onboard volatile storage, which decreases leakage possibilities.
- Keep SSD Firmware Updated:- Outdated firmware versions with security vulnerabilities may enable memory mirroring or flawed cache management. The management of firmware should be performed using manufacturer-specific tools.
- Use Endpoint Detection & Response (EDR):- EDR solutions such as CrowdStrike and Carbon Black monitor systems for unauthorised memory access or dump attempts.
Why It Matters
For Everyday Users:
- The system maintains private data in memory even after shutdown for a brief duration.
- Use encryption and follow proper shutdown procedures while avoiding working with sensitive data on public or shared computers.
For IT and Security Professionals:
- IT professionals should treat SSD DRAM as part of their security threat landscape.
- Establish organisational policies that cover memory cleansing procedures, complete-disk encryption standards, and physical facility protection measures.
Final Thoughts
The risk of memory leakage through volatile storage resembles exposing confidential information on an unprotected kitchen note because intruders can retrieve your entire recipe.
You can protect sensitive information from attackers by understanding data storage locations, implementing encryption measures, and secure shutdown procedures and firmware protection protocols.