Configuring High Availability (HA) Between Two FortiGate Firewalls

Configuring High Availability (HA) Between Two FortiGate Firewalls
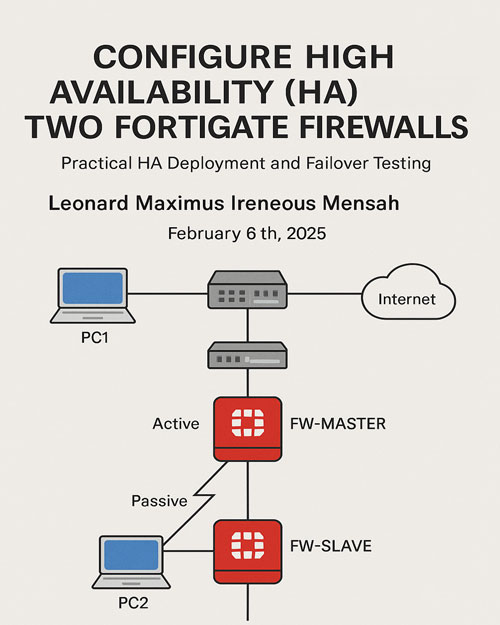
In this project, I configured High Availability (HA) between two FortiGate firewalls to ensure continuous network service during device failure. I began by placing and connecting all required devices on the project board, including two FortiGate units, switches, and two web terminal PCs. I renamed the devices appropriately and established the connections according to the project’s topology goals.
I configured Port 1 and Port 5 on the FG-Master firewall and Port 1 and Port 5 on the FG-Slave firewall with IP addresses 192.168.1.1/24 and 192.168.10.1/24. I then enabled and configured HA on the FG-Master as Primary (Active) and HA on the FG-Slave as Secondary (Passive). I set the correct IP addresses for WebTerm1 and WebTerm2 PCs, ensuring they could communicate through the firewalls.
After configuring the firewalls, I verified that HA was properly established by checking the status, showing FG-Master as Primary and FG-Slave as Secondary. I configured a temporary cloud link on Port 2 of FG-Master to access the management UI and set up the necessary firewall policies to allow traffic between the two networks. Finally, I tested the setup by turning off the FG-Master, observing that the FG-Slave immediately took over as Primary without service disruption. This project demonstrated my ability to implement reliable FortiGate High Availability configurations and validate automatic failover for network resilience.